A sophisticated new phishing-as-a-service (PhaaS) platform named Rockstar 2FA has emerged as a significant threat to Microsoft 365 users, marking a concerning evolution in cybersecurity threats. As reported by BleepingComputer, this advanced phishing toolkit, which has been operational since May 2024, has already established over 5,000 phishing domains and continues to pose an active threat to organizations worldwide.
How Rockstar 2FA works
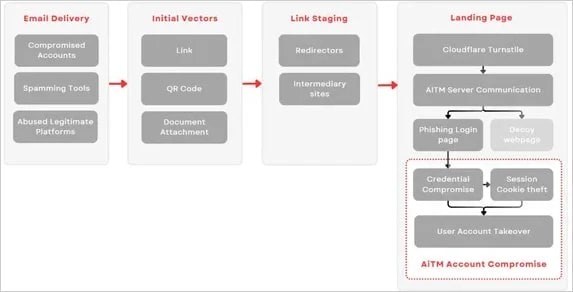
(Image: Trustwave)
The platform employs advanced Adversary-in-the-Middle (AiTM) techniques to bypass traditional security measures, including multi-factor authentication (MFA)[3]. The attack process begins when users are directed to a convincing replica of the Microsoft 365 login page. When victims enter their credentials, the platform’s proxy server forwards these details to Microsoft’s legitimate service while simultaneously capturing the session cookie.
Sophisticated distribution methods
What makes Rockstar 2FA particularly dangerous is its distribution through compromised email marketing platforms, lending legitimacy to its phishing attempts. The campaign utilizes various deceptive messages, including:
- Document sharing notifications
- IT department alerts
- Password reset requests
- Payroll-related communications
Technical capabilities
The platform, available to cybercriminals for $200 for a two-week subscription, includes several advanced features:
- Automated FUD (Fully Undetectable) attachments and links
- Cloudflare Turnstile Captcha integration
- Multiple login page themes with automatic organization branding
- Real-time logging and backup options
Evolution from previous threats
Trustwave security researchers have identified Rockstar 2FA as an updated version of the DadSec and Phoenix phishing kits, which gained notoriety in 2023. Microsoft tracks the developers under the designation Storm-1575, indicating its significance as an emerging threat cluster.
Impact and reach
Since its emergence in May 2024, the platform has seen significant growth, with peak activity recorded in August 2024. The campaign has demonstrated remarkable success in bypassing traditional security measures, making it a particularly concerning threat for organizations relying on Microsoft 365 services.
Security implications
The emergence of Rockstar 2FA represents a significant escalation in phishing capabilities, as it effectively neutralizes one of the most widely recommended security practices – multi-factor authentication. The platform’s success rate and sophisticated approach indicate a new chapter in cybersecurity threats, requiring organizations to reassess their security protocols.
Prevention measures
Organizations using Microsoft 365 should implement additional security layers beyond traditional MFA, including:
- Advanced email filtering systems
- Regular security awareness training
- Monitoring for suspicious login attempts
- Implementation of zero-trust security frameworks
The rise of Rockstar 2FA demonstrates the evolving sophistication of cyber threats targeting Microsoft 365 users. As this threat continues to develop, organizations must remain vigilant and adapt their security measures accordingly.
Discover more from Microsoft News Today
Subscribe to get the latest posts sent to your email.
